The proliferation of digital technology in the last two decades has brought with it a slew of various cyber-threats, especially cybercrime, the most common example of which is data breaches.
The International Organization for Standardization and the International Electrotechnical Commission define a data breach as a compromise of security that leads to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of or access to protected data transmitted, stored or otherwise processed.
For the past several years, bigger data breaches have seemed only moments away as larger breaches have kept coming faster and faster, as stated in the 2017 Verizon Data Breach Investigations Report.
“When a data breach occurs, criminals who steal that data may use it to engage in identity theft,” said Nick Kilmer, assistant director of the Texas A&M Money Education Center. “They might use your personal information to use your credit cards, access your existing accounts or open new accounts in your name.”
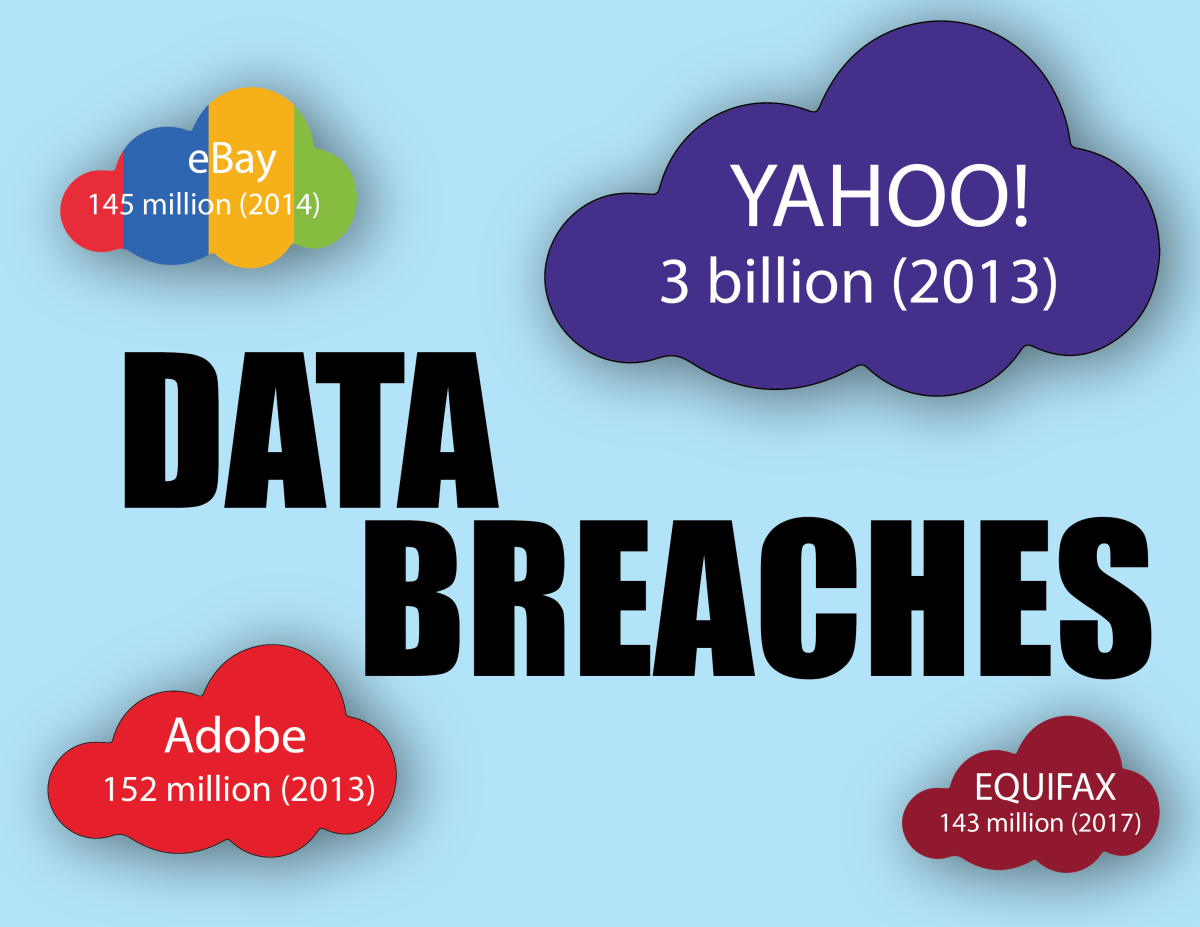
In 2012, 160 million financial records were hacked from various American businesses, including 7-Eleven and the Nasdaq stock exchange. Three billion user accounts were hacked from the web company Yahoo in 2013, which was only disclosed in December of 2016.
Equifax has reported that 143 million Americans have had at least names and Social Security numbers hacked, which means that about half of all households in America are now at greater risk of financial and credit reporting fraud.
“I know personally, I’ve never thought much about the safety of my personal data until a few years ago,” computer science senior Marybeth Villarreal said. “I just never thought about the information I was giving out.”
The best strategy for preventing these type of breaches is to stay diligent about your finances, according to Kilmer.
“It’s in your best interest to regularly review your bank statements, credit card statements and credit reports to check for charges or debts that you don’t remember making yourself,” Kilmer said. “Visit AnnualCreditReport.com for a free credit report every 12 months from each of the three major credit reporting companies. If you see anything out of the ordinary, you should contact each of these credit reporting companies. Identitytheft.gov also provides a list of steps to take to protect yourself against identity theft in the event that you believe that your information has been lost or stolen.”
One of the biggest sources of customer confusion has been the issue of credit freezes versus credit locks, according to Kimer.
“A credit freeze and credit lock are two different ways to protect your credit from identity theft,” Kilmer said. “A credit freeze is more commonly used when consumers believe that their information has been compromised. It blocks lenders from viewing your credit information. Unfreezing your credit report can take several days though. A credit lock is more of a preventative measure. It restricts lender access to your credit information as well, but you can lift the lock immediately if, for example, you’re applying for new a mortgage and need your credit reviewed by a lender. You must contact your credit reporting companies to freeze or lock your credit reports and there may be a one time or recurring a charge for these services.”
On the other side of the Atlantic, the expansive European Union General Data Protection Regulation is set to take effect in May of 2018. Whether the federal government, or state governments in the absence of national action, will follow the lead of the Europeans and mandate businesses to adopt a broad set of data protection principles remains to be seen, according to computer science professor Daniel Ragsdale.
“I do believe that there has to be at least some security standards at the national level,” Ragsdale said. “But the question with regulation is always how much is too much. Where do you draw that line?”
At the moment, the issue of how to protect consumer privacy has divided members of Congress along partisan lines, the most recent example being the repeal of a Federal Communications Commission regulation that required customer approval of data sharing by Internet Service Providers. The measure was approved on a party-line basis.
“I think there is hope,” Ragsdale said. “We are at a point when we are beginning to tip the balance in our favor. Through different efforts including a new generation of cybersecurity professionals like the ones graduating from the Cybersecurity Center here at Texas A&M, I think you are beginning to see a shift. And it is these graduates who are going to be tackling this issue into the future.”
Understanding data breaches
November 15, 2017
0
Donate to The Battalion
$2065
$5000
Contributed
Our Goal
Your donation will support the student journalists of Texas A&M University - College Station. Your contribution will allow us to purchase equipment and cover our annual website hosting costs, in addition to paying freelance staffers for their work, travel costs for coverage and more!
More to Discover